A cache of about 13 gigabytes of stolen images from Snapchat—some of them apparently of nude, underage users of the “ephemeral” messaging platform—was posted online Thursday night, many of them to the image-sharing site 4chan’s /b/ discussion board. However, the threads linking to the images have largely been shut down by 4Chan over concerns of trafficking in what could be considered child pornography. Over 100,000 user images and videos were in the cache, according to 4chan discussions.
The images are apparently not from Snapchat’s own network but from the database of a third-party application that allows Snapchat users to save images and videos sent over the service online. In an official statement to the press, a Snapchat spokesperson said, “We can confirm that Snapchat’s servers were never breached, and were not the source of these leaks. Snapchatters were victimized by their use of third-party apps to send and receive Snaps, a practice that we expressly prohibit in our Terms of Service precisely because they compromise our users’ security.”
According to a report by Business Insider, 4chan users who gained access to the images downloaded them and started to create a searchable database indexed by the usernames associated with the images. The files were also briefly hosted on a Web server that hosted Web exploits and malware.
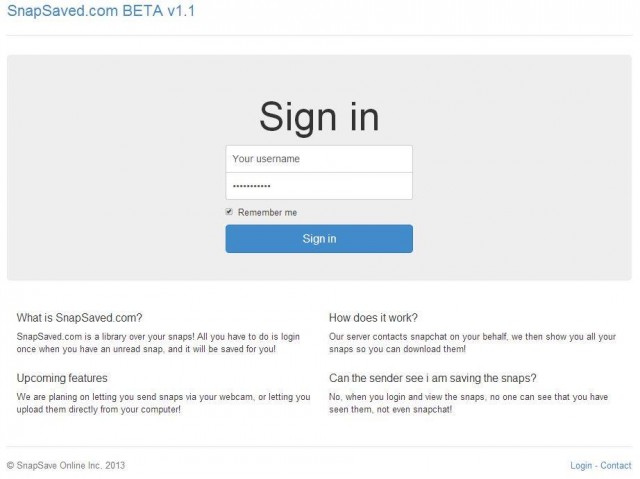
The leak was apparently caused by SnapSaved.com (which has apparently been offline for several months; the link is to the developers’ Facebook page). SnapSaved was a Web-based client built for Snapchat that allowed users to access “snaps” from a Web browser. However, the service, which according to DNS records ran on a server at the hosting company HostGator, apparently kept all images received or sent by its users without their knowledge.
Snapchat does not publish its API for third-party developers, but it has been reverse-engineered. Last year, the company demanded that developer Thomas Lackner remove from GitHub a PHP library he developed called Snaphax, which gives developers access to Snapchat’s API servers, claiming that he had violated the Digital Millennium Copyright Act. Lackner reverse-engineered the API from Snapchat’s official Android client; the code is still on GitHub.
Based on Lackner’s code, Snapchat uses 128-bit AES encryption for images and videos, using a shared secret encryption key that is hard-coded into the client. The key and secret for the Secure Socket Layer Web session used for the API are also hard-coded into the client.
Unless Snapchat made significant changes to its API since then other than the encryption key itself, others could have extracted the key from more recent client code. And even that change is unlikely, as Snapchat would have to turn off access for users who haven’t updated the client—something that doesn’t appear to have happened based on tests using older Snapchat installs on iOS.
There are several applications on both iOS and Android that use a reverse-engineered API to connect to Snapchat—including at least two called SnapSave. But none of these use a cloud storage option or appear to be connected to SnapSaved.com. The login page for SnapSaved, retrieved from the application’s Facebook Page, claims that the website was operated by SnapSave Online Inc.
We have reached out to Snapchat for comment on the status of its API security but have not yet received a response.




0 comments:
Post a Comment